In 1977, Leonid Brezhnev was named Soviet President, Reggie Jackson became baseball’s “Mr. October,” and the RSA asymmetric encryption algorithm was revealed to the public. Well, in 2025, Vladimir Putin has succeeded Brezhnev, Reggie Jackson has been replaced in the collective imagination by Shohei Ohtani and Peter Shor and Schrödinger’s Cat have begun to replace RSA. Let me explain.
Getting past the bare post-quantum facts
Most of us have heard about the advent of post-quantum cryptography and its ramifications: Thanks to Peter Shor’s pioneering work in quantum algorithms, people wielding PQC tools will be capable of arbitrarily decrypting much – if not all – of the data we’re happily encrypting right now. As post-quantum computers become inexorably more capable and available, our secrets won’t remain secret. Before long, PQC tools will target – and defeat – the RSA symmetric encryption algorithm, the Diffie-Hellman key exchange and the Elliptic Curve Digital Signature Algorithm. These constitute the heart of the deeply embedded encryption tools we all use happily every day in our mobile apps, web browsers and critical infrastructure. They work behind the scenes to help keep our secrets safe in our data in transit and our data at rest. We all face a reality where attackers can harvest your data now and then decrypt it later. Isn’t technology democratization fun?
The problem
You see, the computers you know and love use the lowly, but very capable, bit. The bit is very Newtonian: It has two states: 0 and 1 (basically, “on” and off”). The quantum computing “qubit,” which supplants the bit, is post-Newtonian; it can exist in multiple states. In fact it is possible to layer these states in “superposition,” which means these layers combine multiple states between 0 and 1. In the same way a guitar uses multiple strings to create a chord, a quantum computer can create myriad, multiple computing instances to create a powerful chorus of computing power.
The resulting “music,” as it were, is a real-world implementation of Erwin Schrodinger’s thought experiment involving that hapless cat we constantly hear about in these types of discussions: Instead of just being alive or dead, Schrodinger’s quantum cat exists in multiple states inside of that black box. By putting Schrodinger’s analogy to work in the real world, PQC attackers will basically have the ability to throw a wildcat into the cybersecurity and privacy scene and out-compute our traditional encryption algorithms.
To continue the guitar chord analogy, whereas Bo Diddley once brought us his unique boxed guitar beat, we now have many chord permutations, from post- AC/DC arpeggiated power chords to AI-generated Billie Eilish electropop.
Moving beyond theory and FUD: PQC facts and the specter of migration
So, thanks to Shor’s brilliance, a dash of democratization and a huge helping of hacking, you’ve got a nasty reality in just a few years. That’s why the US National Institute of Technology (NIST) has recommended the deprecation of RSA algorithms and related technologies by 2030, and full replacement by 2035. In fact, they have introduced five new computing algorithms.
So, three facts exist about post-quantum computing:
- The 2030 / 2035 dates.
- New PQC algorithms, including the relatively new HQC, as well as BIKE, Classic McEliece, HQC and SIKE.
- PQC migration is a thing: To folks with any experience in IT, this fact brings about a someone chilling conclusion: We’re now facing is yet another long-term rollout. This is a big deal.
A stroll down eternal rollout memory lane
It’s easy to be a bit world-weary about long-term doomsday deadlines. Some of us might remember Y2K. Others might remember when IPv6 was going to complete deployment by, well, whenever. Remember when Linux was going to arrive at the desktop, only to arrive in the Android? We’ve all seen the long rollout of the cloud, as well as zero trust. Most IT leaders are in the midst of bruising, slow-motion rollouts involving compliance to privacy regulations such as GDPR or financial services regulations such as the New York State Department of Financial Services (NYDFS) or critical infrastructure such as the European Union’s NIS2 Directive. With my tongue somewhat in my cheek, I think it’s pretty easy to fall victim to “PQC fatigue syndrome.”
Causes and manifestations of PQC Fatigue Syndrome
IT leaders who have been around any amount of time know what eternal rollouts mean when it comes to PQC: Five years of Fear, Uncertainty and Doubt permeating office, boardroom and server room discussions. Rafts of emails and LinkedIn contacts trying to sell their Post-Quantum Cryptography migration services. Links to paywalled, “nothingburger” articles that provide no more information than a typical Wikipedia entry. Promises of “future-proof” encryption that just don’t deliver. Worried executives who want to make sure that their organizations will remain in compliance.
More practical manifestations are less than amusing: This is yet another high-impact, but low-visibility project that needs to be managed. As a result, IT worker burnout can happen, mainly because workers will need to migrate embedded encryption functions to new algorithms. It’s kind of a thankless task. There’s also a stealth budget impact: Hiring migration services, training workers and doing high-touch encryption incurs real expenses. Sometimes, these expenses aren’t explicitly considered.
Coping mechanisms for PQCFS: Steps for managing tech intolerance
Years ago, it was easy to say, “Executives are tech intolerant,” or that “IT workers just don’t know our business.” But tech intolerance takes much more subtle forms. Organizations still tend to skip steps in software development and infrastructure deployment lifecycles. These are key root cause elements of a technologically tolerant culture. If you want to cope with PQCFS, then it’s necessary to grapple with them. Organizations worldwide can do this by taking two key steps along a long path.
The first step is to improve internal communication. To do this, get two distinct parties to develop a common language – or, to at least understand how they each communicate. Your technical teams must learn to explain any situation, including PQC migration, in both technical and “business” terms. This requires technical workers to learn more
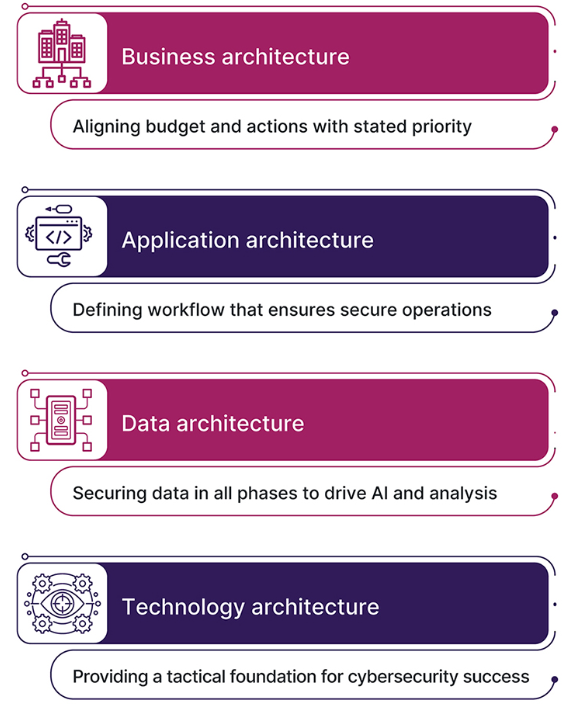
about the nuances of their business. The second party, organizational leaders, need to possess a higher degree of digital fluency. To make this happen, you need a common framework. One thing you can do is divide your PQC migration into separate architectures. At CompTIA, our State of Cybersecurity 2025 report has revealed that creating an enterprise
cybersecurity framework can help. Dividing a project into these architectures or divisions, helps you manage the conversation better. You may find that your organization requires a slightly or even markedly different set of architectures.
A practical way to test if your communication is improving is to gauge how easily and thoroughly your PQC migration plan gets approved. Dividing the discussion into separate architectures and getting plans will be quite an adventure. It’ll involve a lot of steps. But, once you have visualized the architectures, time, resources and skills necessary to do a migration, you can then help an organization move forward into tech tolerance. To me, “tech tolerance” means organizations developing processes that make their operations safe for tech – and humans – to thrive. In this way, project management is more than a task; it’s a way to facilitate tech tolerance.
The second step to moving forward efficiently involves casting the technological details and the FUD into paradigms that might seem new or even irrelevant to techies: Process improvement and Customer Experience. Notice how I didn’t use the terms “risk management” and Governance and Risk Management. As organizations have actually begun to use tech more deeply than ever before, they tend to see technology as facilitators for internal and external communication and interaction. CX involves using technology to help your organization engage in ever-more sophisticated and nuanced dialogs with customers. If you discuss PQC in these terms, you will likely enjoy more success in your long-term budgeting, upskilling and migration efforts. As the PQC long rollout continues, our collective ability to accomplish it relatively smoothly will be a bellwether of our overall maturity as a profession.
